SOC Assurance Reports - The differences
Obtaining assurance over outsourced operations, services, IT systems, and infrastructure is now required by most key stakeholders, whether these are regulators, investors, customers, and/or suppliers. It is now a core part of corporate governance.
It is always better to get in early, as the initial setup of these System and Organisation Control (SOC) assurance reports can absorb considerable time - not to mention costs. Visit our previous article to learn ‘Why your organisation needs a SOC report’.
If your SOC isn’t established correctly, it may result in reputational damage if the control failures are part of the core controls expected of mature or high-profile businesses.
This article presents the different types of SOC assurance reports that should be part of your governance program.
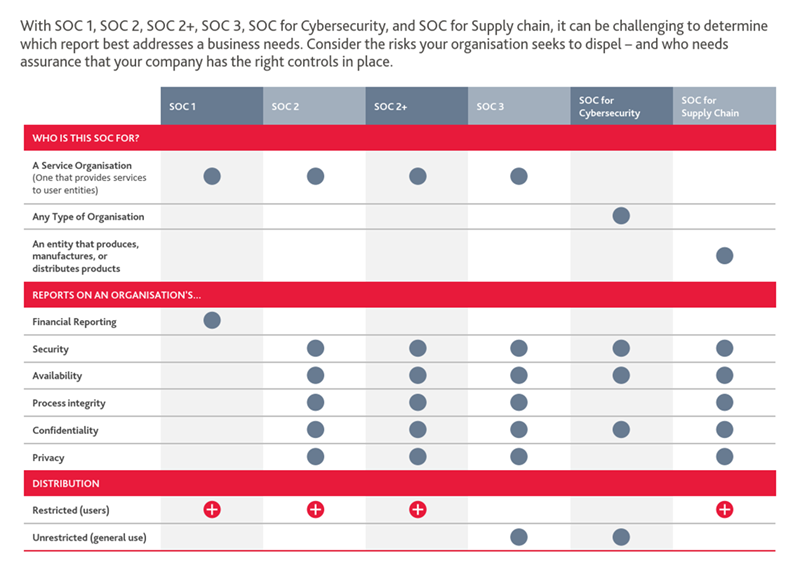
What SOC report do I require?
There are three varying SOC assurance reports - SOC 1, SOC 2, and SOC 3 - each having a ‘Type I’ or ‘Type II’ form of report. For further details on these reports, read our article on ‘Outsourcing – Why your organisation needs a SOC report’.
 An important factor to remember is that the controls to be tested are designed and put forward by the Service Organisation (outsource provider) and the business is not responsible for the operational risks. Therefore, the auditor will (or should) typically encourage a tripartite style meeting with the Service Organisation and their client to determine the scope of coverage and, in particular, the client’s expectations. This protects all parties involved and ensures a level of understanding surrounding scope and reporting outcomes.
An important factor to remember is that the controls to be tested are designed and put forward by the Service Organisation (outsource provider) and the business is not responsible for the operational risks. Therefore, the auditor will (or should) typically encourage a tripartite style meeting with the Service Organisation and their client to determine the scope of coverage and, in particular, the client’s expectations. This protects all parties involved and ensures a level of understanding surrounding scope and reporting outcomes.
An outline of the three SOC Assurance Reports
Systems and Organisation Controls (SOC 1 – Type I & II)
A SOC 1 assurance report focuses on internal controls specified by the Service Organisation (outsource provider). While there should be a customer focus on risks and controls, potential issues are best avoided by ensuring major customers can contribute to the scope.
The assurance work for a SOC 1 assurance report commences with the use of the internal control assertions of the Service Organisation. In Australia, the Independent Assurance Provider uses the Auditing and Assurance Standard ASAE 3402 (international equivalent to ISAE 3402) to deliver the assurance report. Given the sensitive nature of the risks and controls being examined, this is a ‘restricted use’ report and should only be provided to the outsource party’s client and their auditors.
It’s important to remember a SOC 1 assurance report provides an ‘opinion’ on the design and operation of internal controls in relation to ‘historical financial reporting information’. Basically the outsourced financial accounting controls involving financial information and the IT Systems used to secure, manage, process and report financial information that will form the financial statements of the client.
It should be noted that Type I is only for assurance for one day, requiring a walkthrough or ‘test of one’ to confirm the design and operation of the controls on that specific date. A Type II, however, is for a defined period of 6 or 12 months and where control testing is performed over the entire period of reliance.
A Type I is typically only used in limited situations and generally to set up a SOC 1 assurance regime. It focuses on identifying the controls and remediating any control gaps/failures.
The key internal control frameworks are typically based on the universally accepted frameworks, including the Committee of Sponsoring Organisations of the Treadway Commission (COSO) and the Control Objectives for Information and Related Technologies (COBIT).
Systems and Organisation Controls (SOC) 2 – Type I & II
A SOC 2 assurance report has similarities and differences to the SOC 1 report. It is similar in that it focuses on internal controls but is different in that it specifically uses the American Institute of CPA’s (AICPA) established Trust Services criteria (TSC), which covers the five areas of security, privacy, processing integrity, availability, and confidentiality.
The assurance work for SOC 2 commences with the vendor using the Trust Services criteria (as its internal control assertions) to define the basis for the SOC 2 assurance report. In Australia, we also utilise the Auditing and Assurance Standard ASAE 3402 (International equivalent to ISAE 3402) as the primary vehicle to deliver the SOC 2 assurance reports on internal controls.
Given the sensitive nature of the risks and controls being examined, this is also considered a ‘restricted-use’ report and should only be provided to the service organisation’s clients and their auditors. As a general rule, ASAE 3402 reporting is used when the SOC reports are to be distributed by the service organisation to other third-parties and the ASAE 3150 report is used when the SOC report is undertaken by the organisation using a specific service provider and is not for use by other parties.
Recently, the AICPA has allowed service providers and their clients to include additional areas of control within the SOC 2 independent assurance report, over and above the Trust Services Criteria, as they relate to the business ecosystem. As a result, you will see this described as SOC 2+ (Plus). This now enables the SOC 2 assurance report to incorporate other leading frameworks (such as NIST, HITRUST, ISO 27001, HIPPA, CSA, etc.) as they relate to the service providers’ operations.
The report focuses specifically on IT infrastructure and services provided and, unlike SOC 1, does not explore the internal controls about historical financial reporting information.
A Type II report format is the most common, as virtually all outsourced operations utilise technology infrastructure and solutions and require assurance over some time. These are also the most complex and prone to systematic errors.
The types of infrastructure, products, and services typically covered by a SOC 2 assurance report include the following cloud-based or outsourced/managed operations:
- Software as a Service (SaaS)
- Infrastructure as a Service (IaaS)
- Data centres
- Logistical operations, distribution, and supply chains
- Data privacy services
- Cyber services
- Information security services including Security Operations Centres (SOC).
It is important to note this list continues to grow quickly as SOC 2 enables an organisation to obtain assurance over ‘any’ outsourced products or services and compliance-type functions. This also means a broader array of technical specialists is required in fields such as cyber security, data privacy, AI, blockchain, Supply Chain, Engineers, etc.
Systems and Organisation Controls (SOC) 3 – Type II (only)
A SOC 3 Type II assurance report is similar to the SOC 2 Type II assurance report. However, it provides less assurance as it is designed for wider distribution. While SOC 2 (and SOC 1) are ‘restricted-use’ assurance reports, SOC 3 Type II assurance reports are issued for broader distribution.
The SOC 3 assurance report uses the same Trust Services Criteria as the SOC 2 Type II assurance report. However, the report is structured to provide a generic summary of the controls and is designed to be used by vendors who want to put a seal of approval on their websites for marketing purposes. No sensitive information is contained in these reports.
SOC 3 reports are decreasing in popularity with businesses now preferring to obtain SOC 2 Type II assurance reports.
How can we help?
Our professionals provide a full range of SOC 1, 2, 3, ISO Compliance, and other third-party assurance services by applicable professional standards. Our technology risk and control assurance services work closely with our broader Risk team to provide:
- System and Organisation Controls reporting (e.g. SOC 1 & SOC 2 (ASAE 3402/ ASAE 3150)
- APRA Standards - IT Assurance (CPS 220, 231, 232, 233, 234, 235 & the new CPS 230)
- ISO Compliance (27001 Readiness & Maintenance Audits (Pre-Certification))
- IT Governance
- Operational Due Diligence (ODD), including Technology Due Diligence
- Internal IT Controls over Financial Reporting (using COSO & COBIT Frameworks)
- IT Risk & Assurance Control Library Mapping and Control Self-Assessments
- Data Privacy Impact Assessments
- Consumer Data Right (ACCC) Attestation
- Vendor / Third Party Assurance
- Governance, Risk & Compliance Framework Design and Implementation
For more information and to speak to one of our specialists, contact your local BDO adviser.