
Chris Burg
Assisting our clients to identify and address vulnerabilities and weaknesses in their environment.
BDO's experienced team can help you with penetration testing, managed penetration testing, attack simulation and SOC validation and social engineering/red team engagements.
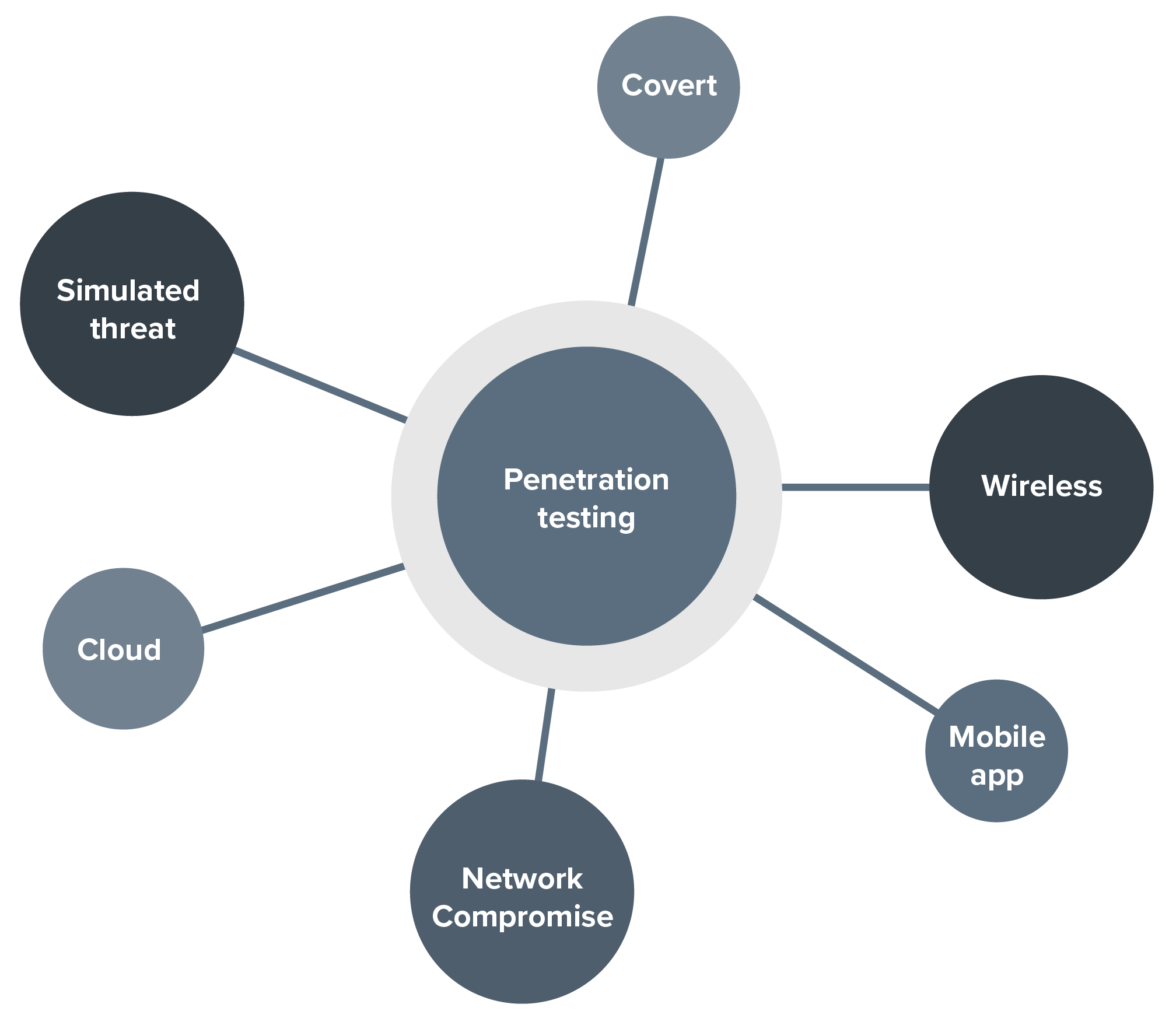
Penetration testing simulates real-world attacks to identify weaknesses by exploiting vulnerabilities, enabling clients to remediate vulnerable areas.
By employing methodologies such as black box, white box, and gray box testing, penetration testing helps organisations enhance their security posture, achieve regulatory compliance, reduce risk, and periodically improve their defences against evolving threats.
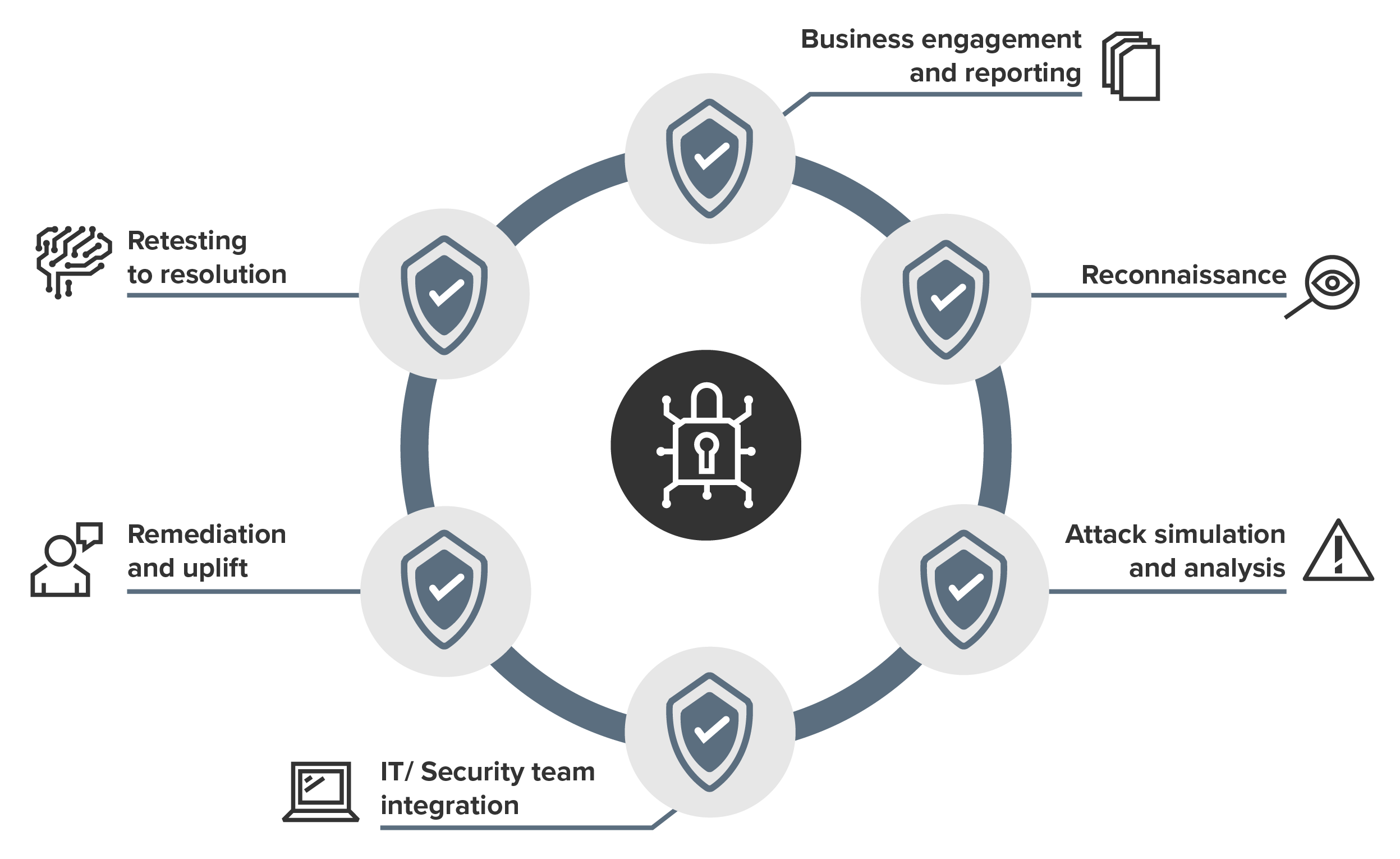
Managed penetration testing provides ongoing testing, analysis, reporting, and remediation support, integrated into IT and information security workflows for continuous risk reduction.
This approach ensures that vulnerabilities are continuously identified and addressed, maintaining an up-to-date security posture.
The process includes regular testing to simulate real-world attacks, detailed analysis to understand vulnerabilities, comprehensive reporting directly into client service desk systems to document findings and provide actionable insights, and ongoing remediation support to assist in fixing identified issues.
By integrating these activities into existing IT and security processes, managed penetration testing helps organisations achieve continuous improvement and robust protection against emerging threats.
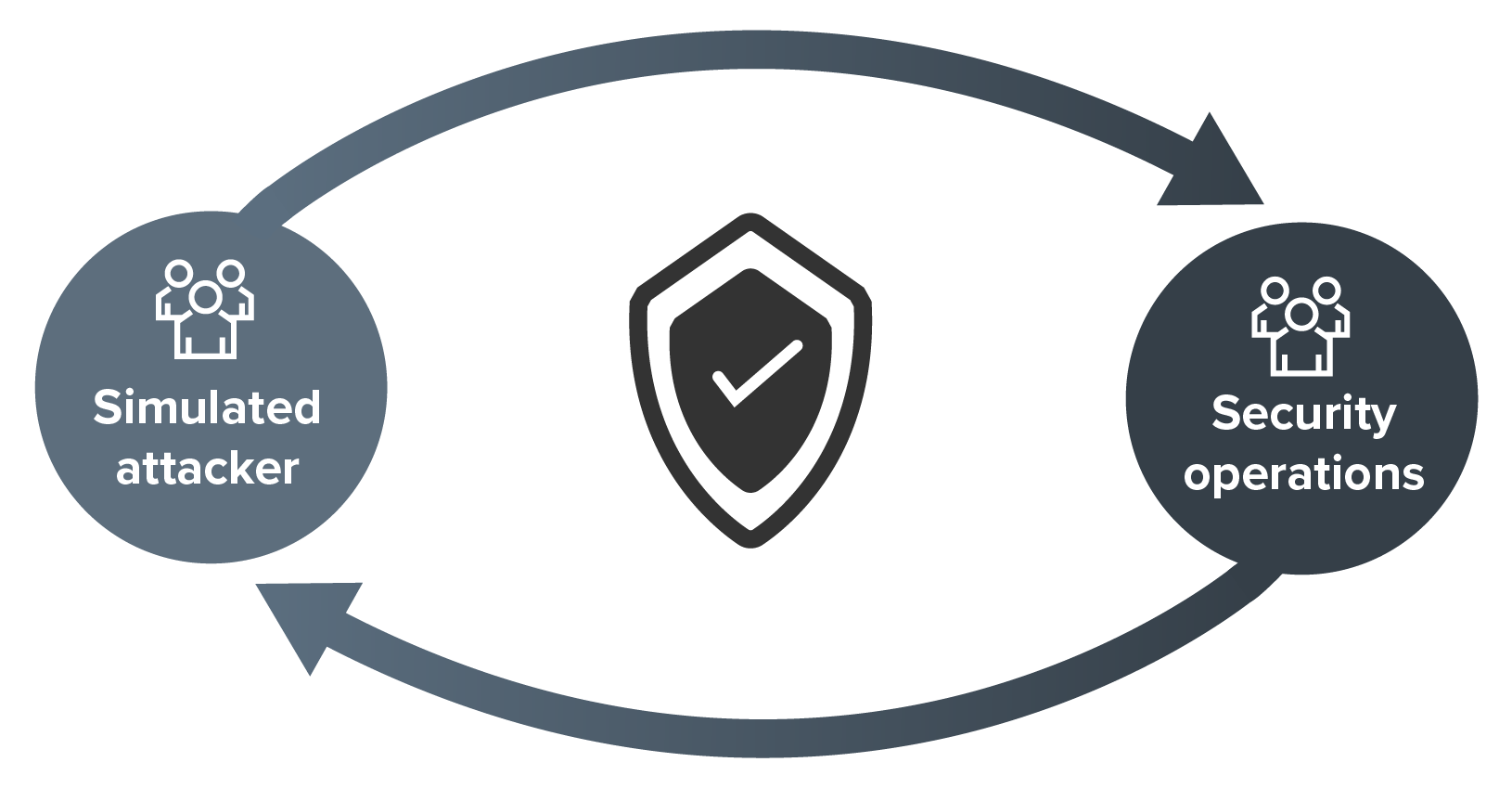
Attack simulation and SOC validation enhances detection and response by simulating attacks and collaborating with the client's security operations team to improve processes and technology.
This service involves simulating realistic attack scenarios to test and evaluate the effectiveness of the Security Operations Centre (SOC).
By working closely with the SOC team, it helps to identify gaps in detection and response capabilities, refine security processes, and optimise the use of technology.
Continuous validation and improvement ensure that the SOC is well-prepared to handle actual cyber threats, ultimately strengthening the organisation's overall security posture.
Social engineering and Red Team engagements simulate adversary tactics to evaluate and improve security controls, identifying vulnerabilities and strengthening defences against sophisticated threats.
These engagements involve realistic attack scenarios that mimic the tactics, techniques, and procedures used by malicious actors, including reconnaissance, phishing campaigns, physical security testing, exploitation, and post-exploitation activities.
The findings are documented in comprehensive reports with risk assessments and detailed remediation recommendations.
This vulnerability assessment approach enhances the organisation's security posture by providing realistic insights into potential attack vectors across people, process and technology, evaluating the effectiveness of existing security controls, raising employee awareness, and improving incident response capabilities.
Contact us
Contact our team to discuss your needs using the request for service form.
Alternatively, call 1300 138 991 to speak with an adviser in your nearest BDO office.

Chris Burg

Mohit Malik

Nick Kervin